Hi Hackers welcome back my new blog post. I hope you are all well. so today this blog we will learn, How To Find Command Injection Vulnerability and How To Get RCE (Remote-Code-Execution) Vulnerability on Web Application. so without wasting your time let's move practical
What is Command Injection 2022
According to OWASP and PortSwigger, Command injection is Typically involves executing commands in a system shell or other part of the environment. and the attacker extent the default functionality of a vulnerable web application. causing it to pass command to the system shell, without needing to inject malicious code in many cases. command injection gives the attacker grater control over the target system.
Command Injection Useful Command
When you have identified an Command Injection Vulnerability, it is generally useful to execute some initial command to obtain info about the system that you have compromised. below is a summary of some commands then are useful for Linux and Windows System.
| Purpose of command | Linux | Windows |
|---|---|---|
| Name of current user | whoami | whoami |
| Operating system | uname -a | ver |
| Network configuration | ifconfig | ipconfig /all |
| Network connections | netstat -an | netstat -an |
| Running processes | ps -ef | tasklist |
Practical. Step-1
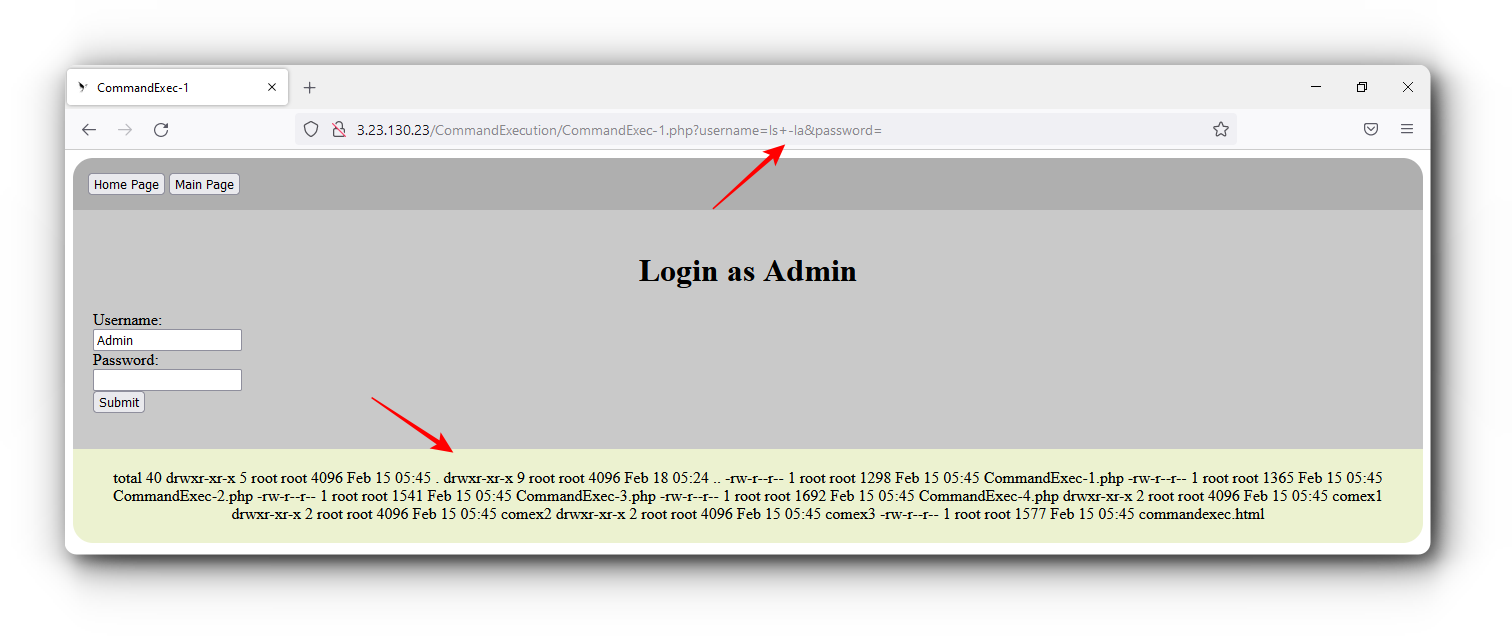
First of all, you have to find out whether the web application on which you are testing is application vulnerable or not. for this you have to find some parameters like name and search on the web application, with this, whatever input you give on the Front-end of the web application can be executed by going to Back-end of the application. If your given malicious command if it reflect and show on the application. then you can understand that command injection exists inside this web application.
Step-2
As you have seen in the above image that we have got command injection on the web application, Now our next step will be that we need to run reverse shell on this web application. so we will use Netcat reverse Shell to perform this process.
Step-3
now we have started listener netcat, Now you have to give a command on the web application, so that it runs on Back-end and we got the reverse shell connection. you can copy the below python command for reverse shell.
Note:- change the IP
Step-4
if your given command gets executed successfully on the web application. Then you can see that you have got the reverse connection of your netcat server.
Command injection to Meterpreter

Step-1
after getting the normal netcat reverse shell, if you want to convert this shell to meterpreter. so for this you have to first create a php shell of a Metasploit. to do this process, I have given you the complete command below. so you can copy and paste your linux terminal.
Next Command:- sed -i 's/#<?php/<?php/' /var/www/html/shell.txt
Step-2
After payload created, then you have to start your Metasploit listener. which will happen that if your shell is executed above the web application then you will get the reverse shell on your Metasploit panel.
Step-4
you can finally see all of this. you have a reverse connection inside Metasploit panel, so that we get to know that our php shell has been successfully executed inside the web application.
Conclusion

so if we talk about conclusion in this post, that is how to find command injection on website 2022, and how to find RCE on Web application 2022. by the way, in this post, I told in detail how you can find remote-code-execution. what if you get command injection inside a web application. so i hope you like this post and i'll see you in the next post. Thanks You Jai Hind.













0 Comments
Please do not enter any spam link in the comment box.